OpenVPN
Virtual Private Network
| 方案 | 区别 |
|---|---|
| 专线 | 不差钱 |
| 硬件 VPN 设备 | 成本低 |
| 开源软件 | pptp(兼容性差)、OpenVPN(数据加密、便于用户可以访问内网,内网) 、IpSEC、OpenSwan |
应用场景
远程访问企业内网
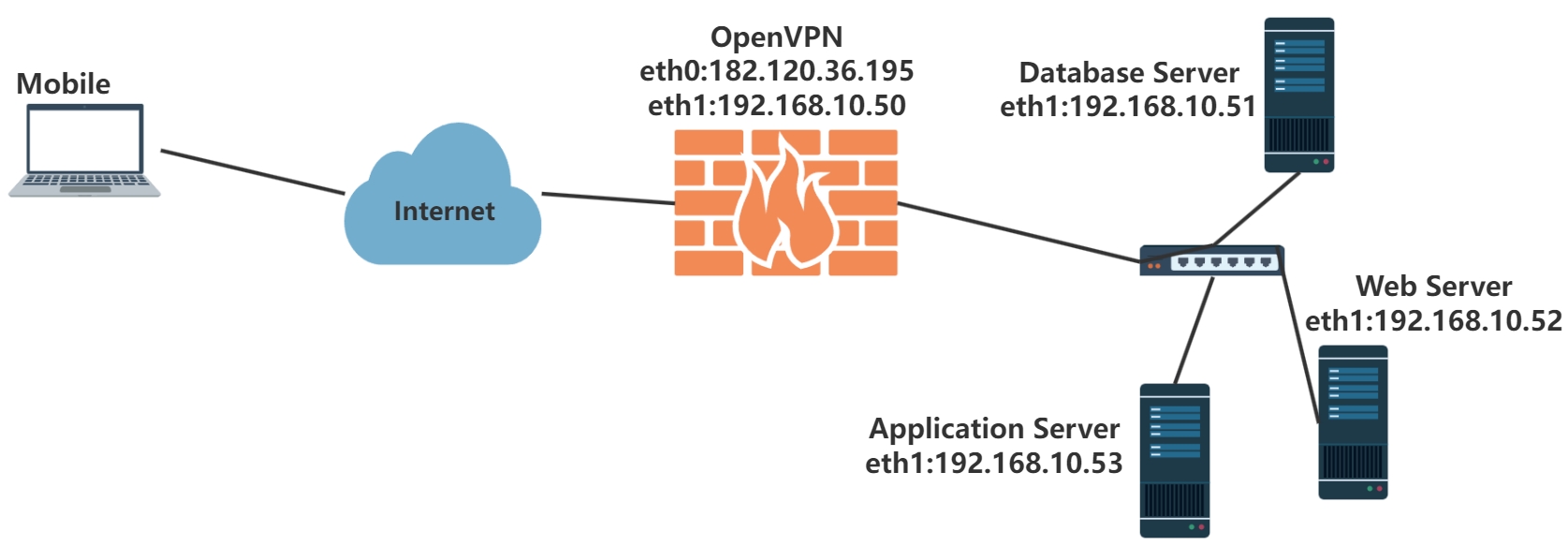
多分支互通
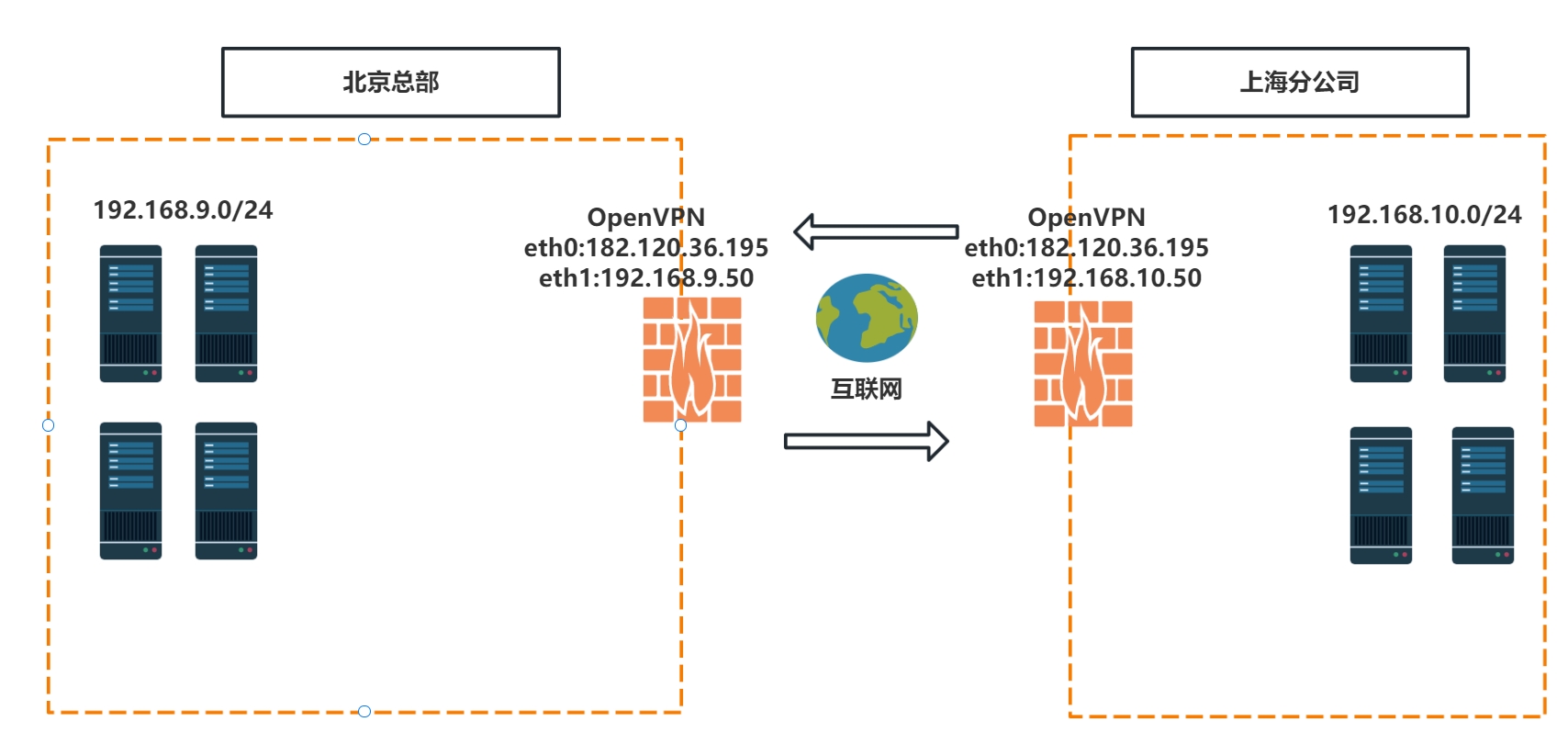
架构
| 角色 | 地址 |
|---|---|
| OpenVPN_Server(开启内核转发功能) | eth0:192.168.10.30/24、eth1:172.16.10.30/24 |
| DB | 172.16.10.31/24 (不需要设置网关,只设置 ip 即可) |
| OpenVPN_Client | 192.168.10.88/24 |
1# 开启内核转发功能
2[root@localhost easy-rsa]# vim /etc/sysctl.conf
3[root@localhost easy-rsa]# sysctl -p
4net.ipv4.ip_forward = 1
CA
| 角色 | 功能 |
|---|---|
| 客户端 | CA 证书:client 密钥(加密) |
| 服务端 | CA 证书:server 密钥(解密) |
| CA | 可以自己创建 |
MariaDB 开启远程访问
1MariaDB [mysql]> GRANT ALL PRIVILEGES ON *.* TO 'root'@'%'WITH GRANT OPTION;
2Query OK, 0 rows affected (0.00 sec)
3
4MariaDB [mysql]> GRANT ALL PRIVILEGES ON *.* TO 'root'@'%' IDENTIFIED BY '123456';
5Query OK, 0 rows affected (0.00 sec)
6
7MariaDB [mysql]> FLUSH PRIVILEGES;
8Query OK, 0 rows affected (0.00 sec)
easy-rsa
创建证书需要一个工具
1### 下载easy-rsa
2[root@zabbixserver ~]# yum install epel-release.noarch -y
3[root@zabbixserver ~]# rpm -Uvh https://mirror.webtatic.com/yum/el7/webtatic-release.rpm
4[root@zabbixserver ~]# curl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.aliyun.com/repo/Centos-7.repo
5[root@zabbixserver ~]# curl -o /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-7.repo
6[root@zabbixserver ~]# yum install easy-rsa -y
7
8
9### 准备vars(充当CA权威机构)
10[root@localhost ~]# mkdir /opt/easy-rsa
11[root@localhost ~]# cd /opt/easy-rsa/
12# 复制目录下所有文件
13[root@localhost easy-rsa]# cp -a /usr/share/easy-rsa/3.0.8/* ./
14[root@localhost easy-rsa]# cp /usr/share/doc/easy-rsa-3.0.8/vars.example vars
15[root@localhost easy-rsa]# egrep -v '^$|^#' vars
16if [ -z "$EASYRSA_CALLER" ]; then
17 echo "You appear to be sourcing an Easy-RSA 'vars' file." >&2
18 echo "This is no longer necessary and is disallowed. See the section called" >&2
19 echo "'How to use this file' near the top comments for more details." >&2
20 return 1
21fi
22# 按需修改
23[root@localhost easy-rsa]# vim vars
24if [ -z "$EASYRSA_CALLER" ]; then
25 echo "You appear to be sourcing an Easy-RSA 'vars' file." >&2
26 echo "This is no longer necessary and is disallowed. See the section called" >&2
27 echo "'How to use this file' near the top comments for more details." >&2
28 return 1
29fi
30set_var EASYRSA_DN "cn_only"
31set_var EASYRSA_REQ_COUNTRY "CN"
32set_var EASYRSA_REQ_PROVINCE "Henan"
33set_var EASYRSA_REQ_CITY "Kaifeng"
34set_var EASYRSA_REQ_ORG "soulboy"
35set_var EASYRSA_REQ_EMAIL "410686931@qq.com"
36set_var EASYRSA_NS_SUPPORT "yes"
37
38# 查看当前目录结构
39[root@localhost easy-rsa]# tree
40.
41├── easyrsa
42├── openssl-easyrsa.cnf
43├── vars
44└── x509-types
45 ├── ca
46 ├── client
47 ├── code-signing
48 ├── COMMON
49 ├── email
50 ├── kdc
51 ├── server
52 └── serverClient
53
54### 1、初始化,在当前目录下创建PKI目录,用于存储证书
55[root@localhost easy-rsa]# ./easyrsa init-pki
56Note: using Easy-RSA configuration from: /opt/easy-rsa/vars
57init-pki complete; you may now create a CA or requests.
58Your newly created PKI dir is: /opt/easy-rsa/pki
59
60[root@localhost easy-rsa]# tree pki
61pki
62├── openssl-easyrsa.cnf
63├── private
64├── reqs
65└── safessl-easyrsa.cnf
66
67### 2、创建CA证书
68[root@localhost easy-rsa]# ./easyrsa build-ca
69
70Note: using Easy-RSA configuration from: /opt/easy-rsa/vars
71Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
72
73Enter New CA Key Passphrase: # 1qaz2wsx
74Re-Enter New CA Key Passphrase: # 1qaz2wsx
75Generating RSA private key, 2048 bit long modulus
76.........+++
77....+++
78e is 65537 (0x10001)
79You are about to be asked to enter information that will be incorporated
80into your certificate request.
81What you are about to enter is what is called a Distinguished Name or a DN.
82There are quite a few fields but you can leave some blank
83For some fields there will be a default value,
84If you enter '.', the field will be left blank.
85-----
86Common Name (eg: your user, host, or server name) [Easy-RSA CA]: # 直接回车
87
88CA creation complete and you may now import and sign cert requests.
89Your new CA certificate file for publishing is at:
90/opt/easy-rsa/pki/ca.crt # 证书的路径和名字
91
92### CA准备完毕
93# 公钥
94 [root@localhost easy-rsa]# cat /opt/easy-rsa/pki/ca.crt
95
96# 私钥
97[root@localhost easy-rsa]# cat /opt/easy-rsa/pki/private/ca.key
98
99
100
101### 3、创建server端证书和私钥文件,请给server端证书签名
102# 创建server端证书和私钥文件,nopass表示不加密私钥文件,其他可默认 (直接回车)
103[root@localhost easy-rsa]# ./easyrsa gen-req server nopass
104req: /opt/easy-rsa/pki/reqs/server.req # 证书请求文件(CA签名之后可以变为公钥)
105 /opt/easy-rsa/pki/issued/server.crt # 被CA签署之后生成的证书会在这里(这里还没有被CA签署完毕)
106key: /opt/easy-rsa/pki/private/server.key # 私钥
107
108# 请给server端证书签名,首先是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码(1qaz2wsx)
109[root@localhost easy-rsa]# ./easyrsa sign server server
110[root@localhost easy-rsa]# ./easyrsa sign server server
111
112Note: using Easy-RSA configuration from: /opt/easy-rsa/vars
113Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
114
115
116You are about to sign the following certificate.
117Please check over the details shown below for accuracy. Note that this request
118has not been cryptographically verified. Please be sure it came from a trusted
119source or that you have verified the request checksum with the sender.
120
121Request subject, to be signed as a server certificate for 825 days:
122
123subject=
124 commonName = server
125
126
127Type the word 'yes' to continue, or any other input to abort.
128 Confirm request details: yes # 这里只能yes
129Using configuration from /opt/easy-rsa/pki/easy-rsa-3453.MVe7kQ/tmp.YN349D
130Enter pass phrase for /opt/easy-rsa/pki/private/ca.key: # CA密码(1qaz2wsx)
131Check that the request matches the signature
132Signature ok
133The Subject's Distinguished Name is as follows
134commonName :ASN.1 12:'server'
135Certificate is to be certified until Jan 1 05:23:16 2026 GMT (825 days)
136
137Write out database with 1 new entries
138Data Base Updated
139
140Certificate created at: /opt/easy-rsa/pki/issued/server.crt # 证书创建完毕
141
142# 创建Diffie-Hellman文件(密钥交换时的Diffie-Hellman算法),需要耗费一些时间
143[root@localhost easy-rsa]# ./easyrsa gen-dh
144DH parameters of size 2048 created at /opt/easy-rsa/pki/dh.pem
145
146### server端通用的CA证书、服务端证书(公钥)和私钥
147/opt/easy-rsa/pki/ca.crt # 服务端通用的CA证书
148/opt/easy-rsa/pki/private/server.key # 服务端公钥
149/opt/easy-rsa/pki/issued/server.crt # 服务端证书(公钥)
150/opt/easy-rsa/pki/private/server.key # 服务端私钥
151
152### 4、创建client端证书和私钥文件,请给client端证书签名
153# 创建client端证书和私钥文件,nopass表示不加密私钥文件,其他可默认 (直接回车)
154[root@localhost easy-rsa]# ./easyrsa gen-req client nopass
155req: /opt/easy-rsa/pki/reqs/client.req # 证书请求文件(CA签名之后可以变为公钥)
156 /opt/easy-rsa/pki/issued/client.crt # 被CA签署之后生成的证书会在这里(这里还没有被CA签署完毕)
157key: /opt/easy-rsa/pki/private/client.key # 私钥
158
159# 请给client端证书签名,首先是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码(1qaz2wsx)
160[root@localhost easy-rsa]# ./easyrsa sign client client
161
162
163### client端证书(公钥)和私钥
164/opt/easy-rsa/pki/issued/client.crt # 服务端证书(公钥)
165/opt/easy-rsa/pki/private/client.key # 服务端私钥
166
167
168### 总结
169/opt/easy-rsa/pki/ca.crt # 通用的CA证书(服务端和客户端都会用到)
170/opt/easy-rsa/pki/dh.pem # 认证算法(服务端用)
171/opt/easy-rsa/pki/issued/server.crt # server 端证书(公钥)
172/opt/easy-rsa/pki/issued/client.crt # client 端证书(公钥)
173/opt/easy-rsa/pki/private/server.key # server 端证书(私钥)
174/opt/easy-rsa/pki/private/client.key # client 端证书(私钥)
部署 OpenVPN 服务端
1### 安装OpenVPN
2[root@localhost easy-rsa]# yum install openvpn -y
3
4# 配置文件模板位置
5/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf
6
7# 配置server端主配置文件(注解版,注解要去掉)
8[root@localhost easy-rsa]# vim /etc/openvpn/server.conf
9port 1194 # 端口
10proto udp # 协议
11dev tun # 采用路由隧道模式tun
12ca ca.crt # ca证书文件位置 默认是/etc/openvpn server端:/etc/openvpn/server 规范可以这样写server/ca.crt
13cert server.crt # 服务端公钥名称 默认是/etc/openvp
14key server.key # 服务端私钥名称 默认是/etc/openvp
15dh dh.pem # 交换证书 默认是/etc/openvp
16server 10.8.1.0 255.255.255.0 # 给客户端分配地址池,注意:不能和VPN服务器内网网段有相同,这里VPN内网网段是172.16.10.0/24
17push "route 172.16.10.0 255.255.255.0" # 允许客户端访问内网172.16.10.0/24网段
18ifconfig-pool-persist ipp.txt # 地址池记录文件位置
19keepalive 10 120 # 存活时间,10秒ping一次,120没有收到响应就视为短线
20max-clients 100 # 最多允许100个客户端连接
21status openvpn-status.log # 日志记录位置 openvpn状态
22verb 3 # openvpn版本
23client-to-client # openvpn多个客户端之间也能互通
24log /var/log/openvpn.log # openvpn日志记录位置
25persist-key # 通过keepalive检测超时后,重新启动VPN,不重新 读取keys,保留第一次使用的keys
26persist-tun # 检测超时后,重新启动VPN,一直保持tun是linkup的,否则网络会先linkdown然后再linkup
27duplicate-cn # 允许每个客户端的公钥私钥相同(所有人密钥一样,但是可以根据密钥创建不同的用户名和密码)
28
29# 配置server端主配置文件(纯净版)
30[root@localhost easy-rsa]# vim /etc/openvpn/server.conf
31port 1194
32proto udp
33dev tun
34ca ca.crt
35cert server.crt
36key server.key
37dh dh.pem
38server 10.8.1.0 255.255.255.0
39push "route 172.16.10.0 255.255.255.0"
40ifconfig-pool-persist ipp.txt
41keepalive 10 120
42max-clients 100
43status openvpn-status.log
44verb 3
45client-to-client
46log /var/log/openvpn.log
47persist-key
48persist-tun
49duplicate-cn
50
51# 复制通用ca证书、server公钥、server私钥、dh.pem文件
52[root@localhost easy-rsa]# cp /opt/easy-rsa/pki/ca.crt /etc/openvpn/ # 通用的CA证书
53[root@localhost easy-rsa]# cp /opt/easy-rsa/pki/issued/server.crt /etc/openvpn/ # server公钥
54[root@localhost easy-rsa]# cp /opt/easy-rsa/pki/private/server.key /etc/openv # server私钥
55[root@localhost easy-rsa]# cp /opt/easy-rsa/pki/dh.pem /etc/openvpn/ # 加密算法文件
56
57# 启动OpenVPN服务
58[root@localhost easy-rsa]# systemctl enable openvpn@server.service
59[root@localhost easy-rsa]# systemctl start openvpn@server.service
60
61# 检查进程
62[root@localhost easy-rsa]# ps -ef | grep openvpn
63root 3843 1 0 15:07 ? 00:00:00 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf
64
65
66# 检查端口
67[root@localhost easy-rsa]# ss -lntup | grep 1194
68udp UNCONN 0 0 *:1194 *:* users:(("openvpn",pid=3843,fd=6))
69
70# 查看启动日志
71[root@localhost easy-rsa]# tail -f /var/log/openvpn.log
72
73Fri Sep 29 15:07:48 2023 OpenVPN 2.4.12 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Mar 17 2022
74Fri Sep 29 15:07:48 2023 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06
75Fri Sep 29 15:07:48 2023 WARNING: --ifconfig-pool-persist will not work with --duplicate-cn
76Fri Sep 29 15:07:48 2023 Diffie-Hellman initialized with 2048 bit key
77Fri Sep 29 15:07:48 2023 ROUTE_GATEWAY 192.168.10.1/255.255.255.0 IFACE=enp0s3 HWADDR=08:00:27:e5:0d:bf # 发现网关
78Fri Sep 29 15:07:48 2023 TUN/TAP device tun0 opened # 添加openvpn虚拟网卡 tun0
79Fri Sep 29 15:07:48 2023 TUN/TAP TX queue length set to 100
80Fri Sep 29 15:07:48 2023 /sbin/ip link set dev tun0 up mtu 1500
81Fri Sep 29 15:07:48 2023 /sbin/ip addr add dev tun0 local 10.8.1.1 peer 10.8.1.2 # 给tun0设置ip 10.8.1.1 10.8.1.2(也是服务端用)
82Fri Sep 29 15:07:48 2023 /sbin/ip route add 10.8.1.0/24 via 10.8.1.2 # 在系统中添加路由信息:只要找10.8.1.0/24 请找 10.8.1.2
83Fri Sep 29 15:07:48 2023 Could not determine IPv4/IPv6 protocol. Using AF_INET
84Fri Sep 29 15:07:48 2023 Socket Buffers: R=[212992->212992] S=[212992->212992]
85Fri Sep 29 15:07:48 2023 UDPv4 link local (bound): [AF_INET][undef]:1194
86Fri Sep 29 15:07:48 2023 UDPv4 link remote: [AF_UNSPEC]
87Fri Sep 29 15:07:48 2023 MULTI: multi_init called, r=256 v=256
88Fri Sep 29 15:07:48 2023 IFCONFIG POOL: base=10.8.1.4 size=62, ipv6=0
89Fri Sep 29 15:07:48 2023 IFCONFIG POOL LIST
90Fri Sep 29 15:07:48 2023 Initialization Sequence Completed
91
92
93# 查看ip地址 发现多一个tun0
94[root@localhost easy-rsa]# ip addr
95 inet 10.8.1.1 peer 10.8.1.2/32 scope global tun0
96
97# 查看路由
98[root@localhost easy-rsa]# yum install net-tools -y
99[root@localhost easy-rsa]# route -n
100Kernel IP routing table
101Destination Gateway Genmask Flags Metric Ref Use Iface
1020.0.0.0 192.168.10.1 0.0.0.0 UG 100 0 0 enp0s3
10310.8.1.0 10.8.1.2 255.255.255.0 UG 0 0 0 tun0
10410.8.1.2 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
105172.16.10.0 0.0.0.0 255.255.255.0 U 101 0 0 enp0s8
106192.168.10.0 0.0.0.0 255.255.255.0 U 100 0 0 enp0s3
部署 OpenVPN 客户端类型
| 客户端类型 | 需要的配置文件及密钥 | 下载地址 |
|---|---|---|
| windows | C:\Program Files\OpenVPN\config[client.ovpn、ca.crt、client.crt、client.key、client.ovpn] | 下载地址 |
| Linux | /etc/openvpn/client/client.conf | |
| 安卓、苹果 |
OpenVPN 客户端:windows
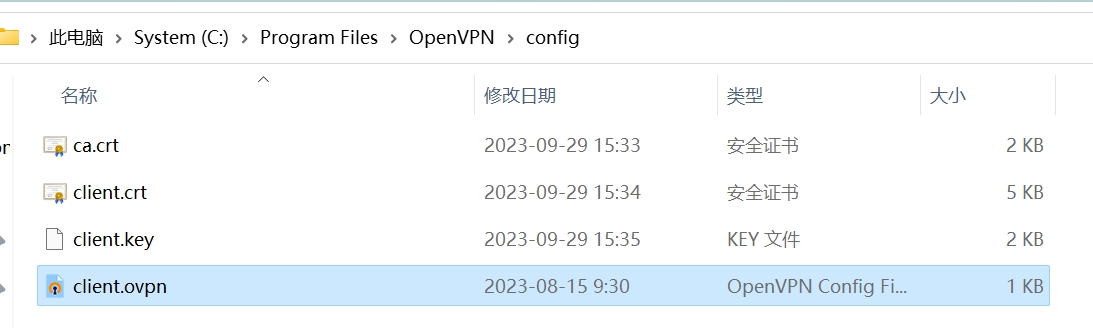
client.ovpn 配置
1### 注解版 C:\Program Files\OpenVPN\config\client.ovpn
2client # 指定当前VPN是客户端
3dev tun # 使用tun隧道传输协议
4proto udp # 使用udp协议传输数据
5remote 192.168.10.30 1194 # openvpn服务器IP地址端口号
6resolv-retry infinite # 断线自动重新连接,在网络不稳定的情况下非常有用
7nobind # 不绑定本地特定的端口号
8ca ca.crt # 指定CA证书的文件路径
9cert client.crt # 指定当前客户端的证书文件路径
10key client.key # 指定当前客户端的私钥文件路径
11verb 3 # 指定日志文件的记录级别,0-9,等级越高日志内容越详细
12persist-key # 通过keepalive检测超时后,重新启动vpn,不重新读取keys,保留第一次使用的keys
13
14### 纯净版 C:\Program Files\OpenVPN\config\client.ovpn
15client
16dev tun
17proto udp
18remote 192.168.10.30 1194
19resolv-retry infinite
20nobind
21ca ca.crt
22cert client.crt
23key client.key
24verb 3
25persist-key
26
27# 查看windows客户端的路由
28C:\Users\chao1>route print
29===========================================================================
30接口列表
31 7...74 56 3c 74 20 7d ......Realtek Gaming 2.5GbE Family Controller
32 53...........................Wintun Userspace Tunnel
33 21...0a 00 27 00 00 15 ......VirtualBox Host-Only Ethernet Adapter
34 54...00 ff 5a 32 ca 1b ......TAP-Windows Adapter V9
35 59...........................OpenVPN Data Channel Offload
36 14...30 05 05 94 07 6a ......Microsoft Wi-Fi Direct Virtual Adapter
37 22...32 05 05 94 07 69 ......Microsoft Wi-Fi Direct Virtual Adapter #2
38 12...30 05 05 94 07 69 ......Intel(R) Wi-Fi 6E AX210 160MHz #2
39 20...30 05 05 94 07 6d ......Bluetooth Device (Personal Area Network)
40 1...........................Software Loopback Interface 1
41===========================================================================
42
43IPv4 路由表
44===========================================================================
45活动路由:
46网络目标 网络掩码 网关 接口 跃点数
47 0.0.0.0 0.0.0.0 192.168.10.1 192.168.10.88 291
48 127.0.0.0 255.0.0.0 在链路上 127.0.0.1 331
49 127.0.0.1 255.255.255.255 在链路上 127.0.0.1 331
50 127.255.255.255 255.255.255.255 在链路上 127.0.0.1 331
51 192.168.10.0 255.255.255.0 在链路上 192.168.10.88 291
52 192.168.10.88 255.255.255.255 在链路上 192.168.10.88 291
53 192.168.10.255 255.255.255.255 在链路上 192.168.10.88 291
54 192.168.56.0 255.255.255.0 在链路上 192.168.56.1 281
55 192.168.56.1 255.255.255.255 在链路上 192.168.56.1 281
56 192.168.56.255 255.255.255.255 在链路上 192.168.56.1 281
57 224.0.0.0 240.0.0.0 在链路上 127.0.0.1 331
58 224.0.0.0 240.0.0.0 在链路上 192.168.56.1 281
59 224.0.0.0 240.0.0.0 在链路上 192.168.10.88 291
60 255.255.255.255 255.255.255.255 在链路上 127.0.0.1 331
61 255.255.255.255 255.255.255.255 在链路上 192.168.56.1 281
62 255.255.255.255 255.255.255.255 在链路上 192.168.10.88 291
63===========================================================================
64永久路由:
65 网络地址 网络掩码 网关地址 跃点数
66 0.0.0.0 0.0.0.0 192.168.10.1 默认
67===========================================================================
68
69
70# 启动openvn客户端
71
72# 再次查看windows客户端的路由
73C:\Users\chao1>route print
74===========================================================================
75接口列表
76 7...74 56 3c 74 20 7d ......Realtek Gaming 2.5GbE Family Controller
77 53...........................Wintun Userspace Tunnel
78 21...0a 00 27 00 00 15 ......VirtualBox Host-Only Ethernet Adapter
79 54...00 ff 5a 32 ca 1b ......TAP-Windows Adapter V9
80 59...........................OpenVPN Data Channel Offload
81 14...30 05 05 94 07 6a ......Microsoft Wi-Fi Direct Virtual Adapter
82 22...32 05 05 94 07 69 ......Microsoft Wi-Fi Direct Virtual Adapter #2
83 12...30 05 05 94 07 69 ......Intel(R) Wi-Fi 6E AX210 160MHz #2
84 20...30 05 05 94 07 6d ......Bluetooth Device (Personal Area Network)
85 1...........................Software Loopback Interface 1
86===========================================================================
87
88IPv4 路由表
89===========================================================================
90活动路由:
91网络目标 网络掩码 网关 接口 跃点数
92 0.0.0.0 0.0.0.0 192.168.10.1 192.168.10.88 291
93 10.8.1.0 255.255.255.0 10.8.1.5 10.8.1.6 225
94 10.8.1.4 255.255.255.252 在链路上 10.8.1.6 281
95 10.8.1.6 255.255.255.255 在链路上 10.8.1.6 281
96 10.8.1.7 255.255.255.255 在链路上 10.8.1.6 281
97 127.0.0.0 255.0.0.0 在链路上 127.0.0.1 331
98 127.0.0.1 255.255.255.255 在链路上 127.0.0.1 331
99 127.255.255.255 255.255.255.255 在链路上 127.0.0.1 331
100 172.16.10.0 255.255.255.0 10.8.1.5 10.8.1.6 225 # 多一条!!!!!!
101 192.168.10.0 255.255.255.0 在链路上 192.168.10.88 291
102 192.168.10.88 255.255.255.255 在链路上 192.168.10.88 291
103 192.168.10.255 255.255.255.255 在链路上 192.168.10.88 291
104 192.168.56.0 255.255.255.0 在链路上 192.168.56.1 281
105 192.168.56.1 255.255.255.255 在链路上 192.168.56.1 281
106 192.168.56.255 255.255.255.255 在链路上 192.168.56.1 281
107 224.0.0.0 240.0.0.0 在链路上 127.0.0.1 331
108 224.0.0.0 240.0.0.0 在链路上 192.168.56.1 281
109 224.0.0.0 240.0.0.0 在链路上 192.168.10.88 291
110 224.0.0.0 240.0.0.0 在链路上 10.8.1.6 281
111 255.255.255.255 255.255.255.255 在链路上 127.0.0.1 331
112 255.255.255.255 255.255.255.255 在链路上 192.168.56.1 281
113 255.255.255.255 255.255.255.255 在链路上 192.168.10.88 291
114 255.255.255.255 255.255.255.255 在链路上 10.8.1.6 281
115===========================================================================
116永久路由:
117 网络地址 网络掩码 网关地址 跃点数
118 0.0.0.0 0.0.0.0 192.168.10.1 默认
119
120# 到此clientOpenVPN连接serverOpenVPN成功,但是数据可以发送过去却没有回应
防火墙设置
1### CentOS 7.0默认使用的是firewall作为防火墙,这里改为iptables
2[root@localhost easy-rsa]# systemctl stop firewalld.service
3[root@localhost easy-rsa]# systemctl disable firewalld.service
4Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
5Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
6[root@localhost easy-rsa]# firewall-cmd --state
7not running
8[root@localhost easy-rsa]# yum install iptables-services
9*filter
10:INPUT ACCEPT [0:0]
11:FORWARD ACCEPT [0:0]
12:OUTPUT ACCEPT [0:0]
13-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
14-A INPUT -p icmp -j ACCEPT
15-A INPUT -i lo -j ACCEPT
16-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
17-A INPUT -p udp -m state --state NEW -m udp --dport 1194 -j ACCEPT # 这里添加!!!!
18-A INPUT -j REJECT --reject-with icmp-host-prohibited
19-A FORWARD -j REJECT --reject-with icmp-host-prohibited
20COMMIT
21
22[root@localhost easy-rsa]# systemctl enable iptables.service
23
24### OpenVPNServer默认监听的端口是1194 ,
25iptables -A INPUT -p udp -m state --state NEW -m udp --dport 1194 -j ACCEPT
解决数据包有去无回:解决方案一:在内网添加路由
1### 在所有内网服务器(DB)上添加路由 (内网服务器网关可以不设置,就算设置了也大概率不应该是172.16.10.30 )
2[root@localhost]# route add -net 10.8.1.0/24 gw 172.16.10.30
3
4# 测试 ping
5C:\Users\chao1>ping 172.16.10.31
6
7正在 Ping 172.16.10.31 具有 32 字节的数据:
8来自 172.16.10.31 的回复: 字节=32 时间<1ms TTL=63
9来自 172.16.10.31 的回复: 字节=32 时间<1ms TTL=63
10来自 172.16.10.31 的回复: 字节=32 时间<1ms TTL=63
11来自 172.16.10.31 的回复: 字节=32 时间<1ms TTL=63
12# 测试 ssh
13C:\Users\chao1>ssh root@172.16.10.31
14The authenticity of host '172.16.10.31 (172.16.10.31)' can't be established.
15ED25519 key fingerprint is SHA256:oodW/8u4n6zqHi2jFk/3lk+1hiD6/Eut3FBB8rbPeAM.
16This key is not known by any other names
17Are you sure you want to continue connecting (yes/no/[fingerprint])?
解决数据包有去无回:解决方案二: 在所有内网服务器设置网关(172.16.10.30 openVPNServer 内网地址)
1### 在所有内网服务器设置网关(172.16.10.30 openVPNServer内网地址)
2[root@localhost ~]# cat /etc/sysconfig/network-scripts/ifcfg-enp0s3
3TYPE="Ethernet"
4PROXY_METHOD="none"
5BROWSER_ONLY="no"
6BOOTPROTO=static
7DEFROUTE="yes"
8IPV4_FAILURE_FATAL="no"
9IPADDR=172.16.10.31
10NETMASK=255.255.255.0
11GATEWAY=172.16.10.30
12IPV6INIT="yes"
13IPV6_AUTOCONF="yes"
14IPV6_DEFROUTE="yes"
15IPV6_FAILURE_FATAL="no"
16IPV6_ADDR_GEN_MODE="stable-privacy"
17NAME="enp0s3"
18UUID="762d2051-2593-430a-ac5b-f3ea57a1b2f9"
19DEVICE="enp0s3"
20ONBOOT="yes"
解决数据包有去无回:方案三:iptables(设置网关 172.16.10.30 openVPNServer 内网地址,同时还可以让内部的服务器通过 openvnpserver 访问互联网)
1### 先决条件:内网的服务器设置网关为192.168.10.30 (openVPNSever的内网地址)
2# 本示例:enp0s3(公网 192.168.10.0/24)、enp0s8(内网 172.16.10.0/24)
3# 公网IP不固定推荐使用:eth0(公网) eth1(私网络)
4iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o eth0 -j MASQUERADE
5iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o enp0s3 -j MASQUERADE
6
7# 公网IP固定可以使用:这里公网ip地址是 enp0s3(公网):192.168.10.30
8iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o eth0 -j SNAT --to-source ip
9iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o enp0s3 -j SNAT --to-source 192.168.10.30
10
11
12# 根据自己情况进行调整 :enp0s3(公网)、enp0s8(内网)
13[root@localhost easy-rsa]# ip addr
141: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
15 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
16 inet 127.0.0.1/8 scope host lo
17 valid_lft forever preferred_lft forever
18 inet6 ::1/128 scope host
19 valid_lft forever preferred_lft forever
202: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
21 link/ether 08:00:27:e5:0d:bf brd ff:ff:ff:ff:ff:ff
22 inet 192.168.10.30/24 brd 192.168.10.255 scope global noprefixroute enp0s3
23 valid_lft forever preferred_lft forever
24 inet6 fe80::8dcb:3e75:9b12:345e/64 scope link noprefixroute
25 valid_lft forever preferred_lft forever
263: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
27 link/ether 08:00:27:4f:dd:37 brd ff:ff:ff:ff:ff:ff
28 inet 172.16.10.30/24 brd 172.16.10.255 scope global noprefixroute enp0s8
29 valid_lft forever preferred_lft forever
30 inet6 fe80::8b4:5697:1f57:159d/64 scope link noprefixroute
31 valid_lft forever preferred_lft forever
328: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 100
33 link/none
34 inet 10.8.1.1 peer 10.8.1.2/32 scope global tun0
35 valid_lft forever preferred_lft forever
36 inet6 fe80::9859:e477:df01:653/64 scope link flags 800
37 valid_lft forever preferred_lft forever
OpenVPN 客户端:Linux
1# 配置文件路径
2[root@localhost easy-rsa]# vim /etc/openvpn/client/client.conf
3client
4dev tun
5proto udp
6remote 192.168.10.30 1194
7resolv-retry infinite
8nobind
9ca client/ca.crt
10cert client/client.crt
11key client/client.key
12verb 3
13persist-key
14
15
16# 启动方式一
17[root@localhost easy-rsa]# /usr/sbin/openvpn --cd /etc/openvpn/ --config client/client.conf
18
19# 启动方式二(推荐)
20[root@localhost easy-rsa]# systemctl cat openvpn@client
21[root@localhost easy-rsa]# vim /usr/lib/systemd/system/openvpn@.service # 修改
22# /usr/lib/systemd/system/openvpn@.service
23[Unit]
24Description=OpenVPN Robust And Highly Flexible Tunneling Application On %I
25After=network.target
26
27[Service]
28Type=notify
29PrivateTmp=true
30ExecStart=/usr/sbin/openvpn --cd /etc/openvpn/ --config client/%i.conf # 哲理需要添加client/
31
32[Install]
33WantedBy=multi-user.target
34
35[root@localhost easy-rsa]# systemctl start openvpn@client
OpenVPN 加密/认证
官方建议
分别为每一个客户端创建证书(虽然安全,但是太繁琐)
| 官方建议 | 拥有者 |
|---|---|
| ca.crt | openvpn 服务端 |
| server.crt | openvpn 服务端 |
| server.key(dh.pem) | openvpn 服务端 |
| ca.crt | openvpn 客户端 01 |
| client1.crt | openvpn 客户端 01 |
| client1.key | openvpn 客户端 01 |
| ca.crt | openvpn 客户端 02 |
| client2.crt | openvpn 客户端 02 |
| client2.key | openvpn 客户端 02 |
最佳实践
所有人的证书和密钥都一样,但以用户名和密码作为区分
| 官方建议 | 拥有者 |
|---|---|
| ca.crt | openvpn 服务端 |
| server.crt | openvpn 服务端 |
| server.key(dh.pem) | openvpn 服务端 |
| ca.crt | openvpn 客户端 01 |
| client.crt | openvpn 客户端 01 |
| client.key | openvpn 客户端 01 |
| 登录的时候输入用户名和密码 soulboy 123456 | |
| ca.crt | openvpn 客户端 01 |
| client.crt | openvpn 客户端 02 |
| client.key | openvpn 客户端 02 |
| 登录的时候输入用户名和密码 leon 654321 |
自定义脚本实现认证功能
1### 1、修改OpenVPNSever端主配置文件:开启支持自定义脚本
2# 注解版
3[root@localhost easy-rsa]# vim /etc/openvpn/server.conf # 追加
4script-security 3 # 允许使用自定脚本
5auth-user-pass-verify /etc/openvpn/check.sh via-env # 指定认证脚本路径
6username-as-common-name #用户密码登录方式验证
7
8# 纯净版
9[root@localhost easy-rsa]# vim /etc/openvpn/server.conf # 追加
10script-security 3
11auth-user-pass-verify /etc/openvpn/check.sh via-env
12username-as-common-name
13
14
15### 2、编写/etc/openvpn/check.sh 认证脚本
16# 定义脚本
17[root@Web01 ~]# vim /etc/openvpn/check.sh
18#!/bin/bash
19PASSFILE="/etc/openvpn/openvpnfile" # 密码文件 用户名 密码明文 (中间通过空格分隔)
20LOG_FILE="/var/log/openvpn-password.log" # 用户登录情况的日志
21TIME_STAMP=`date "+%Y-%m-%d %T"`
22if [ ! -r "${PASSFILE}" ]; then
23 echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
24 exit 1
25fi
26CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
27if [ "${CORRECT_PASSWORD}" = "" ]; then
28 echo "${TIME_STAMP}: User does not exist: username=\"${username}\",password=\"${password}\"." >> ${LOG_FILE}
29 exit 1
30fi
31if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
32 echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
33 exit 0
34fi
35echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
36exit 1
37
38
39# 修改脚本权限
40[root@localhost easy-rsa]# chmod 600 /etc/openvpn/check.sh
41[root@localhost easy-rsa]# chmod +x /etc/openvpn/check.sh
42
43### 3、创建用户(不需要在系统中存在,在/etc/openvpn/openvpnfile文件中存在即可)
44# 创建用户(空格作为分隔)
45[root@localhost easy-rsa]# vim /etc/openvpn/openvpnfile
46soulboy 123456
47leon 654321
48
49# 重启openvpnserver服务
50[root@localhost easy-rsa]# systemctl restart openvpn@server.service
openvpn 客户端配置
1### 修改客户端配置文件 C:\Program Files\OpenVPN\config\client.ovpn
2# 追加
3auth-user-pass
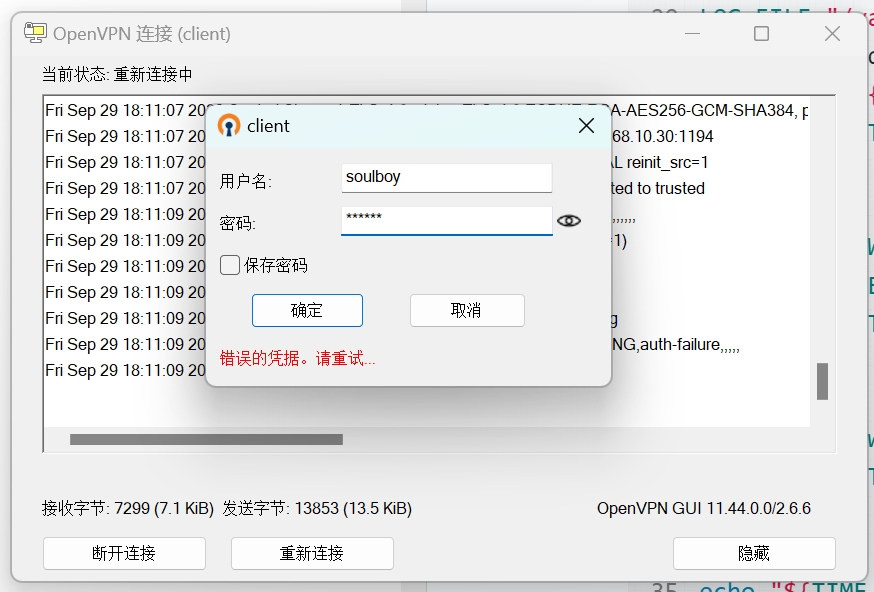
1### OpenVPNServer 查看日志 /var/log/openvpn-password.log
2[root@localhost easy-rsa]# tail -f /var/log/openvpn-password.log
32023-09-29 18:11:08: User does not exist: username="asd",password="asd".
42023-09-29 18:11:32: Successful authentication: username="soulboy".
补充
1### 自动化
2wget -O openvpn.sh https://get.vpnsetup.net/ovpn
3sudo bash openvpn.sh --auto
4
5### 备用脚本地址
6https://github.com/hwdsl2/openvpn-install/raw/master/openvpn-install.sh
7https://gitlab.com/hwdsl2/openvpn-install/-/raw/master/openvpn-install.sh
8
9
10### OpenVPN 客户端(全平台)
11https://openvpn.net/vpn-client/
12
13### 安卓OpenVPN
14https://apkcombo.com/tw/openvpn/net.openvpn.openvpn/download/apk